Risk Management
- Risk management vision:
(1) Undertake to continue to provide products and services to create long-term value for customers, shareholders, employees and society.
(2) Risk management must have systematic risk management procedures and organizations to identify, evaluate, process, report and monitor major risks that affect the companys's viability, and enhance the risk awareness of allemployees.
(3) Risk management is not the pursuit of "zero" risk, but the pursuit of maximum benefit under the condition of acceptable risk to optimize the risk management cost. - Risk management policy:
(1) Ensure the company's sustainable operation, establish a risk management committee, and identify, evaluate, process, report, and monitor the risks that may negatively affect the company's operating goals every year.
(2) Identify and control risks before an accident occurs, suppress losses when an accident occurs, and quickly resume product and service provision after an accident; and formulate a business continuity plan for major risk scenarios identified by the Risk Management Committee.
(3) For the risk that does not exceed the risk tolerance, the risk management cost must be considered and treated with different management tools, but the following conditions are not limited to this.
●Negative impact on the safety of employees.
●Negative impact on the company’s goodwill.
●Cause violation of laws and regulations.
To effectively control risk management, the Risk Management Committee (RMC) implements the construction, implementation, supervision, and maintenance of risk management plans. The committee effectively monitors risks through risk self-assessment reports and specific improvement plans for risk improvement plans, , analyze risk distribution and formulate risk improvement guidelines by managing annual reports.
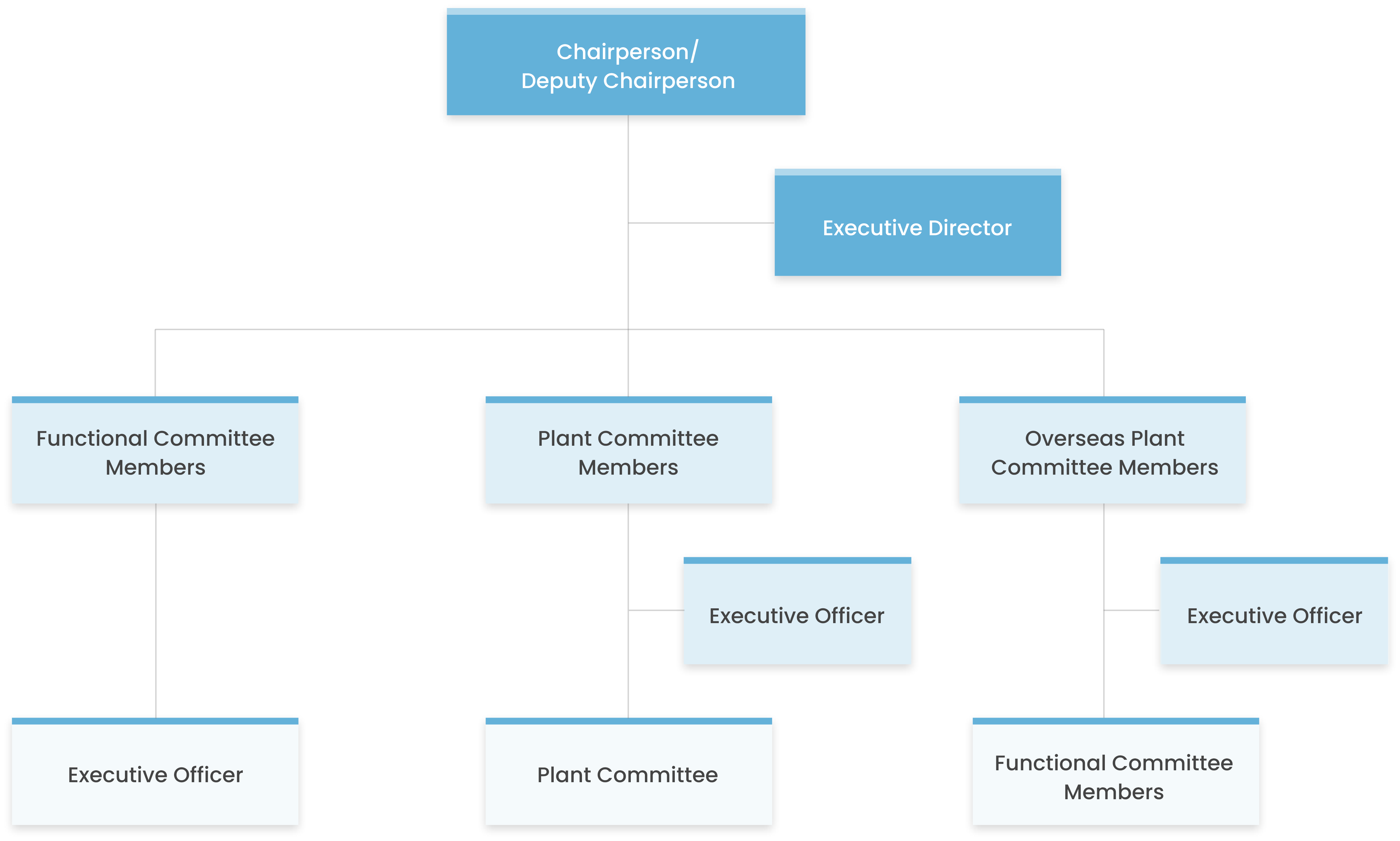
Risk Management Committee Organization
Impact and risk of information system
In view of the current emerging information security attack trends, such as ransomware, social attacks, and counterfeit emails, which seriously threaten the information security of global companies and individuals. In order to protect the company's rights and the goal of sustainable operation, it has established establish a safe and reliable computerization operating environment to ensure the safety of the company's computer data, systems, equipment, network and maintain normal operation. The company has established the "Information Security Policy Procedures" and the "Information Security Practices" formulated in accordance with the framework in accordance with the ICT Security Management Law, Personal Data Protection Law, Copyright Law, Electronic Signature Law and other regulations. The audit department shall conduct regular audits and report to the board of directors in accordance with the established measures.




